Friday, December 9, 2016
Friday, December 2, 2016
Problem & Solution: Can't install jdk 8 on Ubuntu using PPA
Hello Friends.. :)
Problem: initially I tried to install java9 using PPA. Everything was going well but due to some network problem installation failed. Then tried java 8 again failed. Just tried java 7..worked Ye!!
But again wanted to install Android Studio.. Downloaded and tried to install but got error that it require java >=8
OO.. now tried again PPA command but couldn't worked
Solution: Tried installing java 8 manually.
Ref. : https://itsfoss.com/install-java-ubuntu-1404/
Problem: initially I tried to install java9 using PPA. Everything was going well but due to some network problem installation failed. Then tried java 8 again failed. Just tried java 7..worked Ye!!
But again wanted to install Android Studio.. Downloaded and tried to install but got error that it require java >=8
OO.. now tried again PPA command but couldn't worked
Solution: Tried installing java 8 manually.
Ref. : https://itsfoss.com/install-java-ubuntu-1404/
Thursday, December 1, 2016
How to be a successful teenage entrepreneur
1.Model Success
2. Get Experience
3. Take Consistent action
Sunday, November 27, 2016
MALICIOUS SOFTWARE
Definition : Any software that brings harm to a computer system.
Various Malware's:
1.Spyware :
Spyware is any technology that aids in
gathering information about a person or
organization without their knowledge.
2. Logic Bomb :
code embedded in legitimate program activated when specified conditions met
3. Trojan Horse :
program with hidden side-effects which is usually superficially attractive
4.Zombie :
program which secretly takes over another networked computer
5. Virus :
a piece of self-replicating code attached
to some other code and propagate itself
by carrying codes
6. Worms :
A standalone malware computer program that replicates itself in order to spread to other computers
Tuesday, November 22, 2016
Monday, November 21, 2016
SD3 Framework
SD3 Security Framework
Secure by Design:
- Security in product development process
- Building Threat model and threat analysis
- conduct code reviews
- secure architecture
- Vulnerability reduction
Secure By Default:
- Default installation and usage with minimum surface for attack
- Unused feature turned off by default
- Minimum privileges used
- Built in functions for defense in depth
Security By Deployment:
- protection: Detection,Defense,recovery,management,Leverage the security best practices
- Process: Create security guidance
- People: build tool to access application security,give them training
What Is the Smart Grid?
The smart Grid is developing network of transmission lines,equipment,
controls and new technologies working together to respond immediately
to our 21st century demand for electricity.
Traditional about hundred yrs ago,
- Localised Power generation
- Small Energy Demands
- One way interaction(From station to home)
Smart grid to meet 21st century electricity demand:
>2 way dialogue: electricity and information can be exchanged between
utilities and customers
>Developing network working together to make grid more efficient,reliable,secure,greener
>Provide newer technologies to be integrated such as Wind ,Solar productions and
Plugin electric vehical charging
>Smart home communicates with grid and enbles consumers to manage electricity usage
>By measuring home electricity consumtion frequently by using smart meter
utilities can provide much more information to customer to manage their electric bills.
>Inside smart home,through HAN device can be connected to energy managment system
>Smart appliances and devices can adjust their run schedules do reduce energy demard
at critical time and lower energy bills
>This smart devices can be scheduled over web or even over TV
>Renewable enery sources and sustainable energy sources but are variable by nature
and add complexity to normal grid operation
>Smart grid provide data and automation needed to enable solar panel and wind forms
to put enery on to grid and optimize its use
>
>Defering Electric usage
Friday, November 18, 2016
Apriori Algorithm
Apriori Algorithm
a,d,e,NaN
b,c,d,NaN
a,b,c,d
b,c,NaN,NaN
a,b,d,NaN
d,e,NaN,NaN
a,b,c,NaN
c,d,e,NaN
a,b,c,NaN
"""
from itertools import combinations
import pandas as pd
trans=pd.read_csv('output.txt',header=None)
print (trans)
def apriori(trans,support=0.01,minlen=1):
ts=pd.get_dummies(trans.unstack().dropna()).groupby(level=1).sum()
collen,rowlen=ts.shape
pattern=[]
for cnum in range(minlen,rowlen+1):
for cols in combinations(ts,cnum):
patsup=ts[list(cols)].all(axis=1).sum()
print(patsup,'\n')
patsup=float(patsup)/collen
pattern.append([",".join(cols),patsup])
sdf=pd.DataFrame(pattern,columns=['Pattern','Support'])
results=sdf[sdf.Support >= support ]
return results
print (apriori(trans))
ts=pd.get_dummies(trans.unstack().dropna()).groupby(level=1).sum()
collen,rowlen=ts.shape
"""
output.txt
a,b,c,NaNa,d,e,NaN
b,c,d,NaN
a,b,c,d
b,c,NaN,NaN
a,b,d,NaN
d,e,NaN,NaN
a,b,c,NaN
c,d,e,NaN
a,b,c,NaN
"""
from itertools import combinations
import pandas as pd
trans=pd.read_csv('output.txt',header=None)
print (trans)
def apriori(trans,support=0.01,minlen=1):
ts=pd.get_dummies(trans.unstack().dropna()).groupby(level=1).sum()
collen,rowlen=ts.shape
pattern=[]
for cnum in range(minlen,rowlen+1):
for cols in combinations(ts,cnum):
patsup=ts[list(cols)].all(axis=1).sum()
print(patsup,'\n')
patsup=float(patsup)/collen
pattern.append([",".join(cols),patsup])
sdf=pd.DataFrame(pattern,columns=['Pattern','Support'])
results=sdf[sdf.Support >= support ]
return results
print (apriori(trans))
ts=pd.get_dummies(trans.unstack().dropna()).groupby(level=1).sum()
collen,rowlen=ts.shape
Thursday, November 17, 2016
Matplotlib Various styles to Plot : Very SImple
Matplotlib Simple Basic Program: Lets try various line styles
1. import matplotlib.pyplot as plt
2. plt.plot([1,2,3,4],[1,3,8,2]')
3. plt.axis([0,10,0,10])
4. plt.show()
Lets know step by step:
1. import required library i.e here we want pyplot
2. plot() -> awsome method...
syntax:
plot(<values of x axis>,<values of y axis>,<style and format>)
So here x values are [1,2,3,4] and y values are [1,3,8,2] it means plot method will map values of x to y as in sequence i.e. (1,1),(2,3),(3,8),(4,2)
3. axis() -> by default length of x and y axis are as much as required only. But you can still specify how much you want.
syntax: axis(<list specifying range of x,y>)
i.e. axis([<begin_x>,<end_x>,<begin_y>,<end_y>])
So here we will draw x axis ranging from 0 to 10 and y from 0 to 10
4. Finally show() will actually plot on screen. :)
Output:

2. plt.plot([1,2,3,4],[1,3,8,2],"r-") 3. plt.plot([1,4,7,9],[1,3,8,2],"r--")
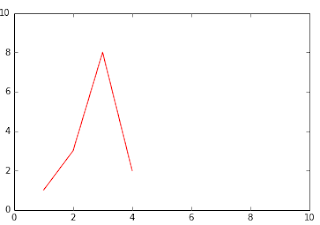

4. "gr-." : green color Dashed Dot 5. 'c:' cyan dotted line style


6. 'm.' : magenta point marker 7. 'yo' yellow circle marker


8. 'kv' black triangle_down marker 9.'^' triangle_up marker


10. '<' triangle_left marker 11. '>' triangle_right marker


12. '1' tri_down marker (2,3,4 for up,left,right respectively)

13.'s' square marker 14.'p' pentagon marker


15. '*' star marker 16. 'h' hexagon1 marker


17. 'H' hexagon2 marker 18.'+' plus marker

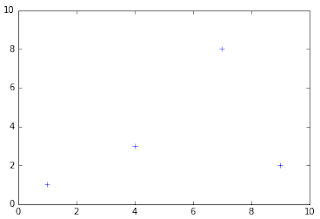
19. 'x' x marker 20. 'D' diamond marker

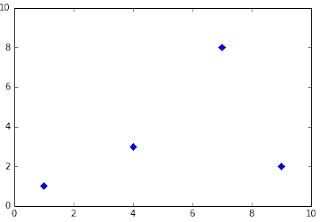
21.'d' thin_diamond marker 22. '|' vline marker

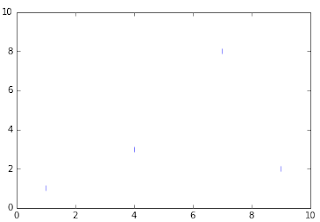
23. '_' hline marker

Saturday, September 10, 2016
Performance Metrics for Parallel Systems
Fig.IBM's Blue Gene/P massively parallel supercomputer.
Q.1 Define Speedup, efficiency, cost of parallel system.
Speedup :
> Speedup measures increase in running time due to parallelism
> No. of PEs = n
> Based on running time :
Speedup S= Ts/Tp where
Ts = Execution Time on single processor, using fastest known sequential algorithm
Tp = Execution Time using parallel processor i.e.
Efficiency
Cost
Cost = parallel running time x number of processors
> Also called “Algorithm cost” for clarity
> Parallel algorithm whose cost is big-oh of running time of optimal sequential algorithm is called “Cost optimal”
Q.2. Explain cost optimal algorithm for addition of n numbers on p processors where p <<n.
Steps :
- Distribute n/p elements to p PEs.
- Each processor adds n/p elements locally in O(n/p).
- Propagate partial sums up a logical binary tree of PEs in O(log p).
Parallel Runtime :
As long as n=O(plogp), Cost is O(n) which is same as serial runtime. Hence Cost-Optimal.
Fig. cost optimal way of adding 16 numbers using 4 PEs
Wednesday, August 24, 2016
Explain SIMD and MIMD with its architecture
SIMD [ Single Instruction, Multiple Data ] :
> All processing units execute the same instruction at any given clock cycle
> Each processing unit can operate on a different data element
> Best suited for specialized problems characterized by a high degree of regularity, such as graphics/image processing
> Synchronous (lockstep) and deterministic execution
> Two varieties: Processor Arrays and Vector Pipelines
> Most modern computers, particularly those with graphics processor units (GPUs) employ SIMD instructions and execution units.
> All processing units execute the same instruction at any given clock cycle
> Each processing unit can operate on a different data element
> Best suited for specialized problems characterized by a high degree of regularity, such as graphics/image processing
> Synchronous (lockstep) and deterministic execution
> Two varieties: Processor Arrays and Vector Pipelines
> Most modern computers, particularly those with graphics processor units (GPUs) employ SIMD instructions and execution units.
MIMD [ Multiple Instruction, Multiple Data ] :
> Every processor may be executing a different instruction stream
> Every processor may be executing a different instruction stream
> Every processor may be working with a different data stream
> Execution can be synchronous or asynchronous, deterministic or non- deterministic
> Currently, the most common type of parallel computer - most modern supercomputers fall into this category.
> Many MIMD architectures also include SIMD execution sub-components
What is meant by shared memory parallel computer? Explain its advantages and disadvantages.
General Characteristics:
> all processors can access all memory as global address space
> Multiple processors can operate independently
> If any processor modify any memory location, visible to other processors
> Historically, shared memory machines have been classified as UMA and NUMA, based upon memory access times.
Fig. UMA Fig. NUMA
Advantages:
> Global address space provides a user-friendly programming perspective to memory
> Data sharing between tasks is both fast and uniform due to the proximity of memory to CPUs
Disadvantages:
> Lack of scalability between memory and CPUs.
Adding more CPUs can geometrically increases traffic on the shared memory-CPU path, and for cache coherent systems, geometrically increase traffic associated with cache/memory management.
> Programmer responsibility for synchronization constructs that ensure "correct" access of global memory.
Who use Parallel Computing?
Companies that I know which are working in parallel computing area are Intel , IBM, calligo tech, TCS and Wipro.




 Fields :
Fields :
-
Science and Engineering
-
Industrial and Commercial
-
Global Applications
Science and Engineering
Industrial and Commercial
Global Applications
What is Parallel Computing and Why Use Parallel Computing?
Serial Computing:
In Serial Computing, problem is broken down into instructions that are execute on single processor one at time.Parallel Computing:
In Parallel Computing, problem is broken down into discrete parts. These parts are further broken down into instructions execute sequentially. Ultimately, Discrete parts can execute concurrently on different processor.Advantages :
- SAVE TIME AND/OR MONEY
- as cheap, commodity components can be used
- SOLVE MORE COMPLEX PROBLEMS
- as no limiting computing like traditional
- PROVIDE CONCURRENCY
- as we use multiple processor
- TAKE ADVANTAGE OF NON-LOCAL RESOURCES
- by wide area network
- MAKE BETTER USE OF UNDERLYING PARALLEL HARDWARE
- as modern laptops also based on parallel architecture
Subscribe to:
Comments (Atom)




